¶ Description
Extract data from Cryptographic Signatures.
¶ Parameters
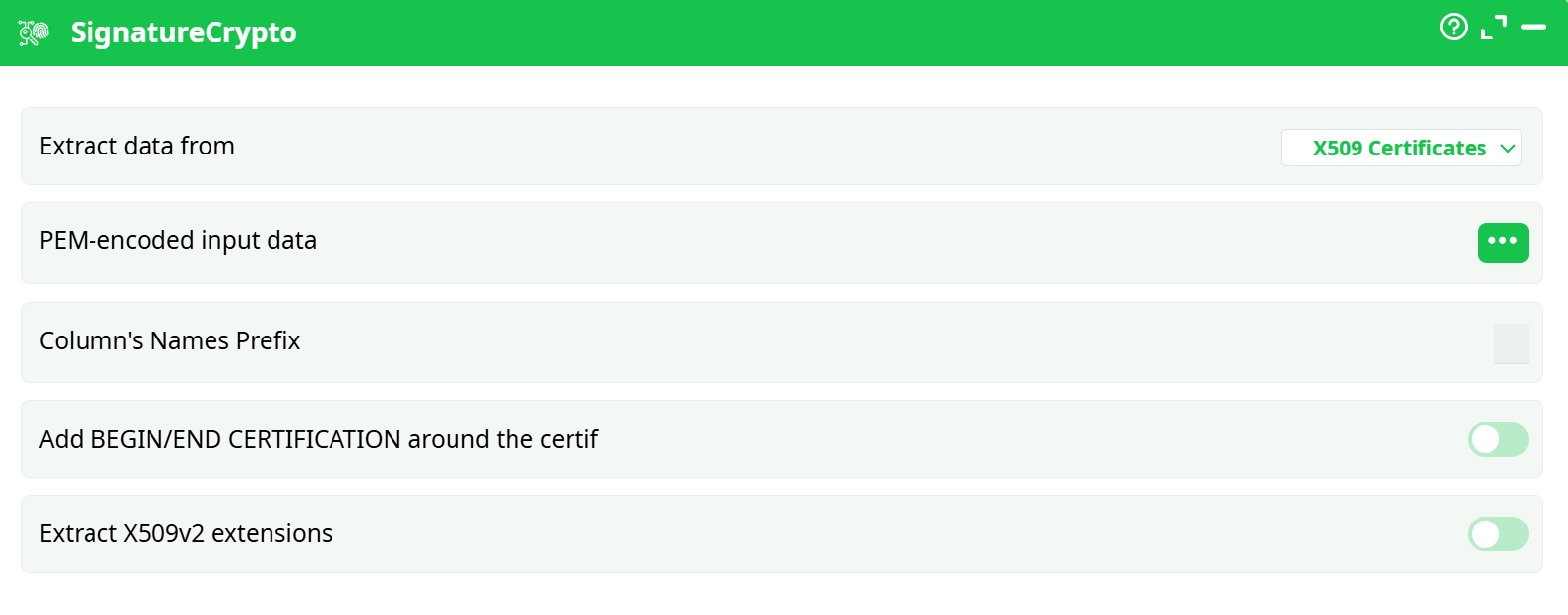
Parameters
- Extract data from Type of cryptographic object to parse. Options:
X509 Certificates,PKCS7 Signatures - PEM-encoded input data Column containing raw PEM certificate or signature text
- Column's Names Prefix Optional prefix for all generated output column names
- Add BEGIN/END CERTIFICATION around a certif Automatically wrap certificate body with standard PEM headers/footers if missing
- Extract X509v2 extensions Enables extraction of extra certificate metadata like SAN, CRL, policies, etc.
¶ About
The SignatureCrypto action is used to extract metadata from digital signatures or X.509 certificates provided in PEM format. It supports decoding:
- X.509 Certificates
- PKCS7 Signatures
This action is useful in certificate validation, PKI data processing, and cryptographic audits.
¶ Example Input (CSV)
pem_certificate
"-----BEGIN CERTIFICATE-----
MIIDXTCCAkWgAwIBAgIJAKC7Va4O6ZilMA0GCSqGSIb3DQEBCwUAMEUxCzAJBgNV
...
-----END CERTIFICATE-----"
¶ Output Fields (Prefixed with cert_)
| Column | Description |
|---|---|
cert_Status |
Shows Success or Error based on parsing outcome |
cert_Certificate_Serial_Number |
Certificate serial number |
cert_Subject |
Subject (who the certificate is issued to) |
cert_Issuer |
Issuer (who issued the certificate) |
cert_NotBefore |
Certificate validity start |
cert_NotAfter |
Certificate expiry date |
cert_Public_Key |
Public key |
cert_Email, cert_Purpose, etc. |
Optional fields extracted when extensions are enabled |
If cert_Status shows Error, most output fields will be null.
¶ Usage Example
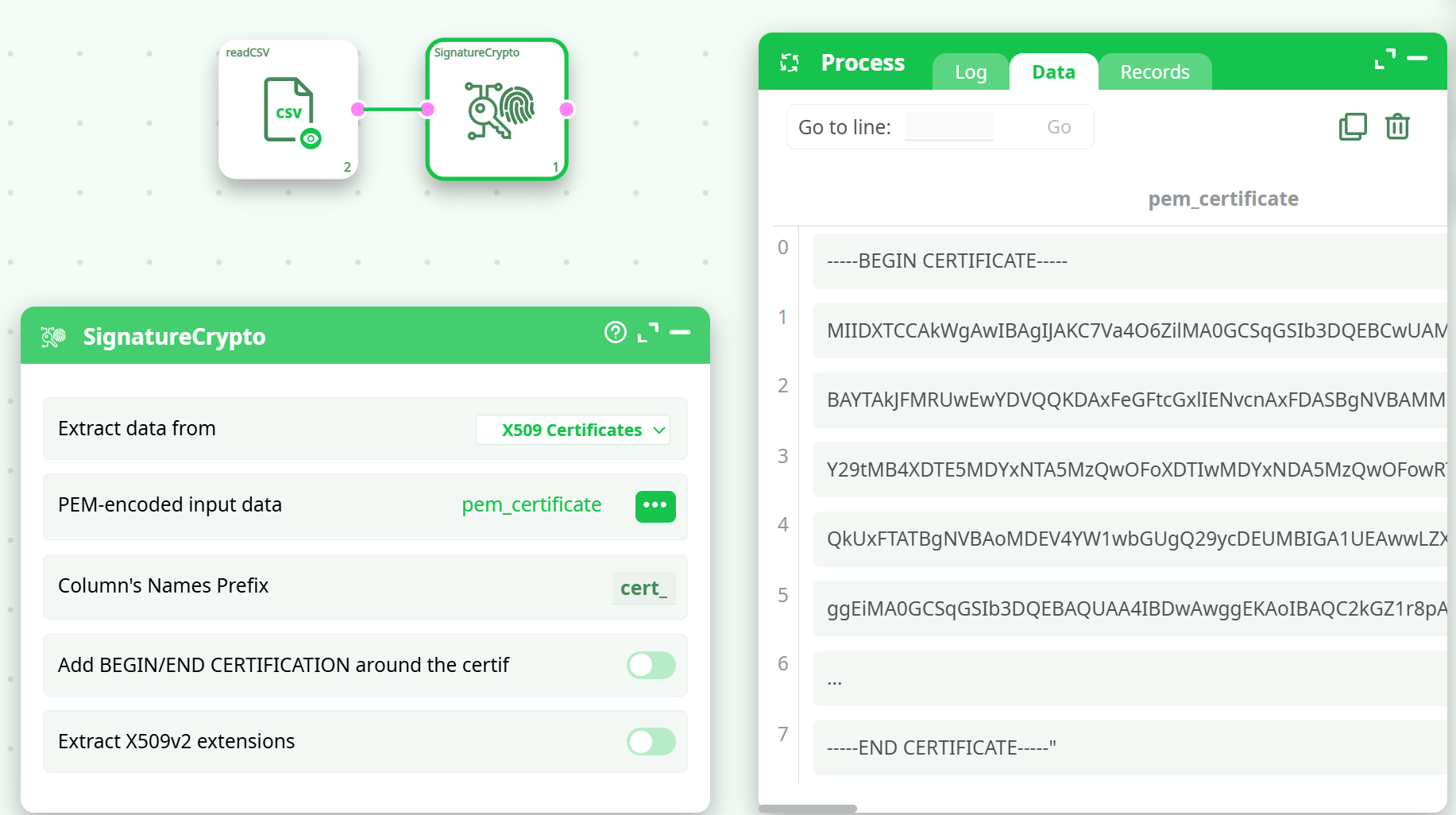
- Input Source
- Use readCSV or readTXT with a column pem_certificate containing PEM strings.
- Action Setup
- Extract data from: X509 Certificates
- PEM-encoded input data: pem_certificate
- Column's Names Prefix: cert_
- Disable Add BEGIN/END CERTIFICATION (as headers are present)
- Disable Extract X509v2 extensions (optional)
- Run Pipeline
- Output columns like cert_Status, cert_Issuer, cert_NotAfter will be created if successful.
¶ Troubleshooting
- If you see Error in cert_Status, try:
- Verifying PEM block is fully intact and not split across lines in CSV
- Enabling "Add BEGIN/END CERTIFICATION" if headers are missing
- Using readTXT instead of readCSV to maintain multiline formatting
- Testing with a known good certificate (e.g., from openssl or browser exports)
¶ Screenshots
Notes
- This action is designed for PEM-encoded content only. DER/binary formats must be converted prior to input.
- The action will fail if the PEM data is line-broken in CSV. Prefer readTXT for loading full PEM blobs.
- In production, validate with test certs and adjust toggles (BEGIN/END, extensions) as needed.
