¶ Description
Encrypt a column using SHA256 hashing algorithm.
¶ Parameters
¶ Parameters tab
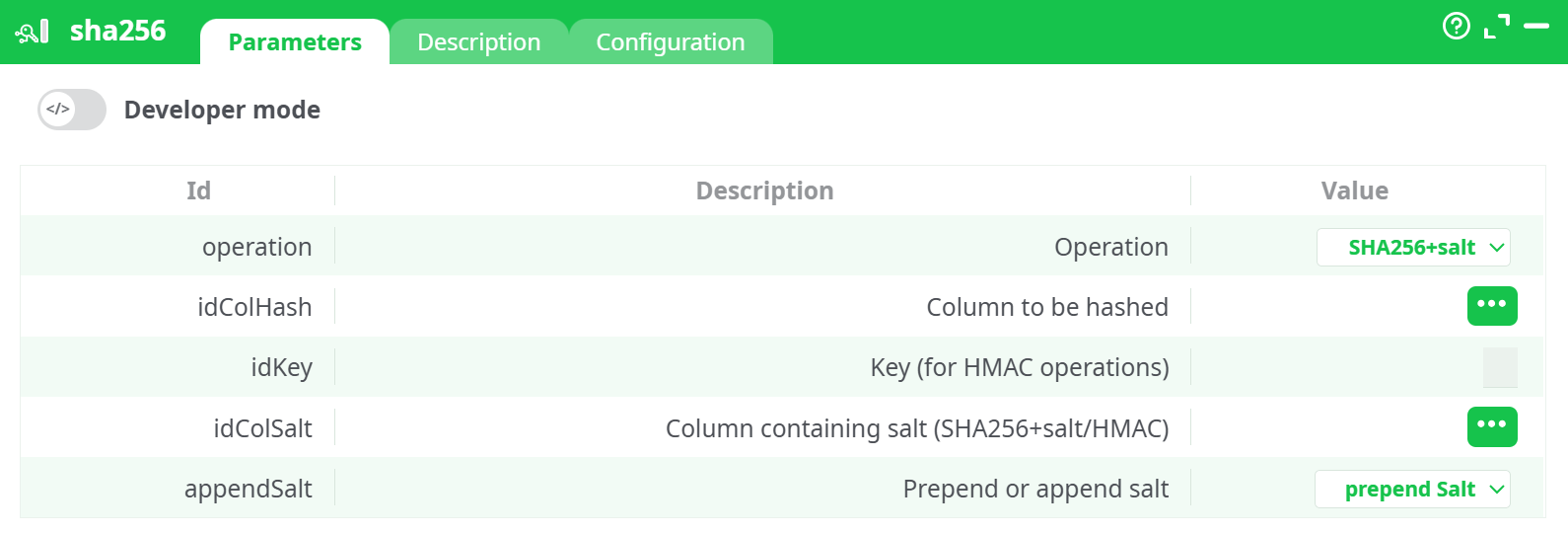
Parameters:
- Developer mode: activate/deactivate code tab.
- Operation Defines the type of hashing operation to apply.
- Column to be hashed Column containing the string to be hashed.
- Key (for HMAC operations) Secret key column used only when
operation = HMAC. - Column containing salt (sha256+salt/HMAC) Column containing the salt value (used for salt & HMAC).
- Prepend or append salt Determines if the salt should be prepended or appended.
¶ Description tab
See dedicated page for more information.
¶ Code tab
sha256 is a scripted action. Embedded code is accessible and customizable through this tab.
¶ Configuration tab
See dedicated page for more information.
¶ About
The sha256 action computes a secure hash from an input string using the SHA-256 algorithm. It supports multiple operation modes including plain SHA-256, SHA-256 with salt (prepend or append), and HMAC-SHA256 using a secret key. This action is commonly used for secure password hashing, token generation, and verifying data integrity within ETL pipelines.
This action button hashes an input column using one of the following methods:
- SHA256 – A standard SHA-256 hash of the selected column.
- SHA256+salt – Adds a salt (from another column) either before or after the value before applying SHA-256.
- HMAC – Generates a HMAC using SHA-256, with a secret key from another column.
This is a useful tool in data transformation workflows to securely encode sensitive data such as passwords or identifiers.
⚠️ Security Note: Always ensure salts and secret keys are managed securely and not reused improperly. HMAC is ideal when authentication is required.
¶ Operation Modes & Examples
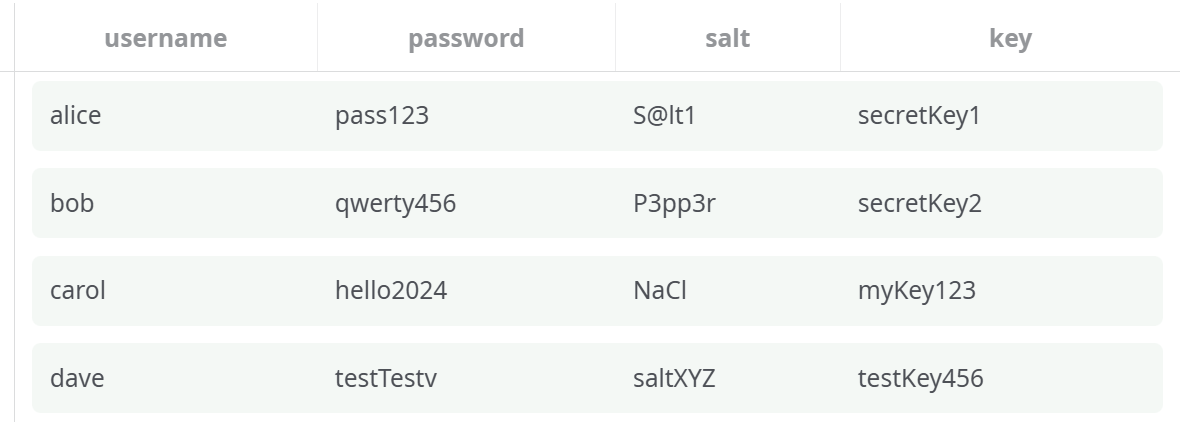
Example Input:
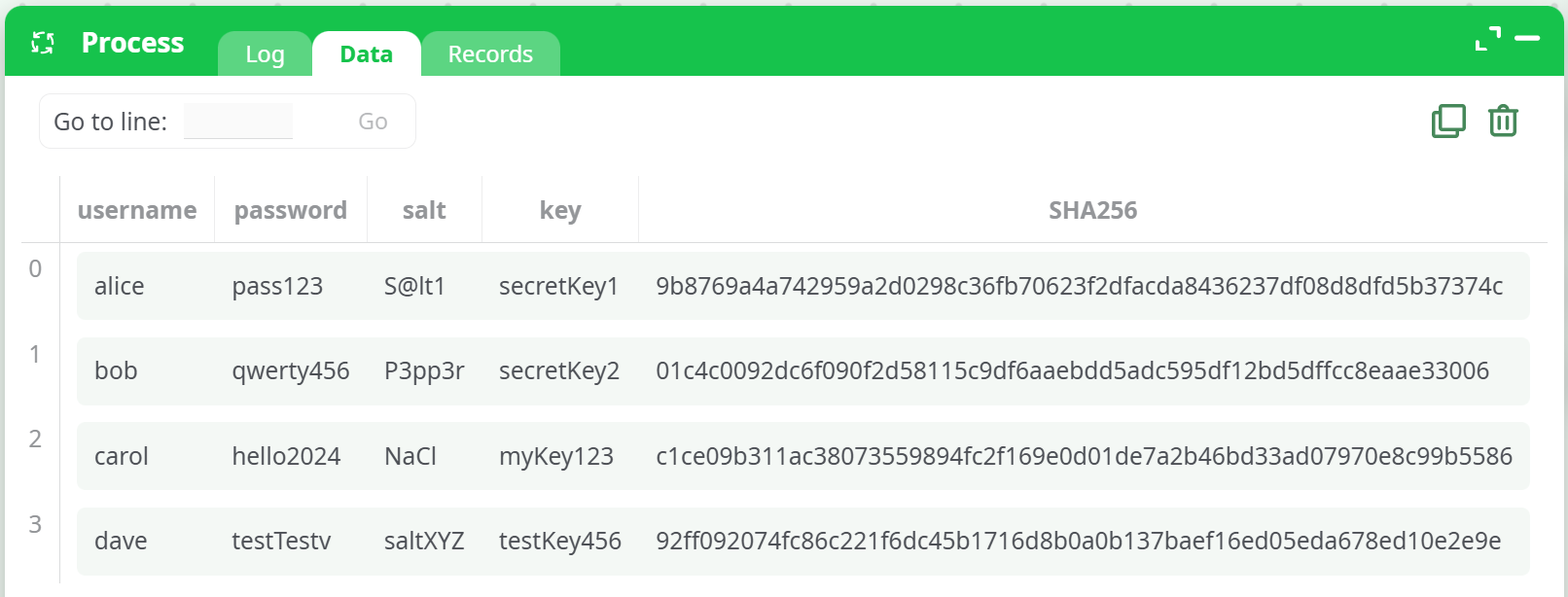
¶ 1. SHA256
Applies SHA256 directly to the string without salt or key.
Action Configuration:
operation:SHA256idColHash:password
Example Output:
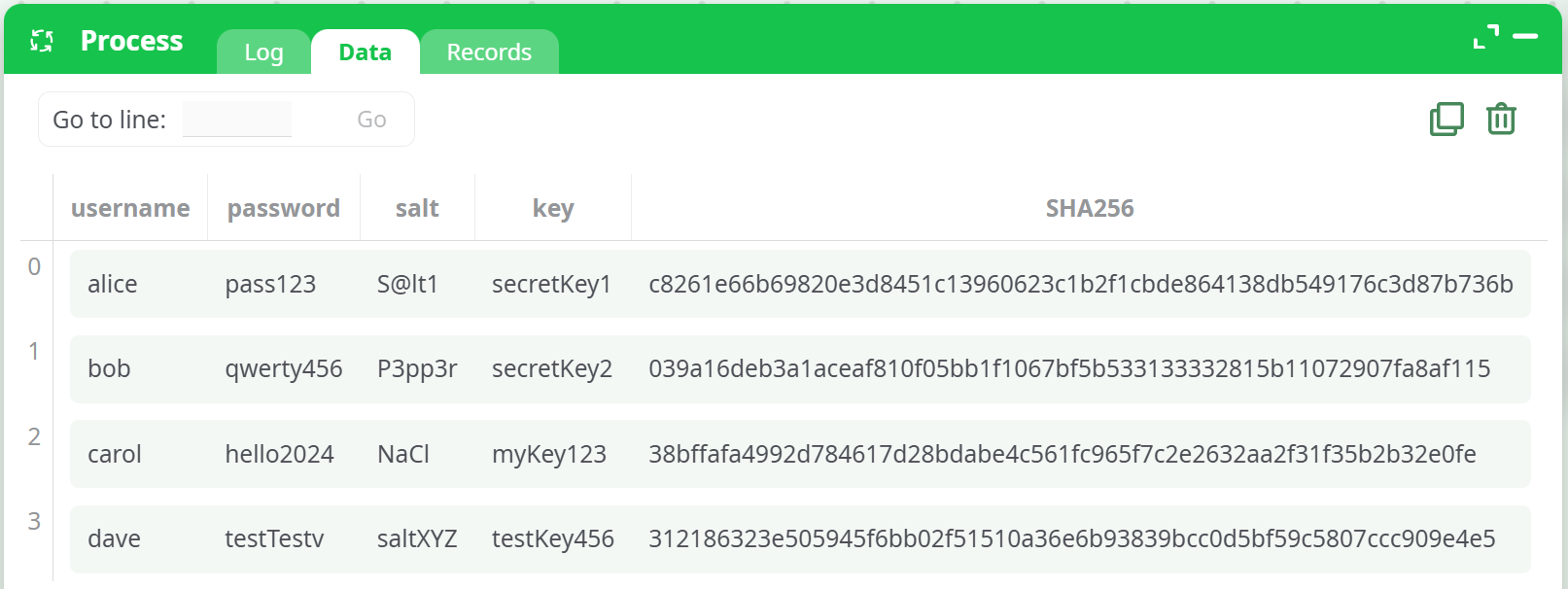
¶ 2. SHA256 + Salt (Prepend)
Prepends the salt before hashing. Useful for basic password hashing techniques.
Action Configuration:
operation:SHA256+saltidColHash:passwordidColSalt:saltappendSalt:prepend Salt
Computation:
SHA256(salt + password)
Example Output:
¶ 3. SHA256 + Salt (Append)
Appends the salt after the input string.
Action Configuration:
operation:SHA256+saltidColHash:passwordidColSalt:saltappendSalt:append Salt
Computation:
SHA256(password + salt)
Example Output:
| password | salt | SHA256 |
|---|---|---|
| pass123 | S@lt1 | 1260385a18242e2cf9891b1bb4afb28... |
¶ 4. HMAC
Creates a keyed hash using HMAC with SHA-256. More secure for authentication and integrity checks.
Example Input:
| username | password | key |
|---|---|---|
| alice | pass123 | secretKey1 |
Action Configuration:
operation:HMACidColHash:passwordidKey:key
Computation:
HMAC-SHA256(password, key)
Example Output:
| password | key | SHA256 (HMAC) |
|---|---|---|
| pass123 | secretKey1 | 9b8769a4a742959a2d0298c36fb706... |
¶ Usage Tips
- If
SHA256+saltis selected and theidColSaltis left blank, the action behaves like plainSHA256. HMACrequires theidKeyfield to be filled; otherwise, the hash result may be empty or error-prone.- Use
prependSaltwhen your system expects salts before the data, andappendSaltotherwise. - Make sure to keep all salt and key fields secured if dealing with real user data.
¶ Example Pipelines
¶ Pipeline 1: Secure Password Hashing
- Input via
InlineTableor other input buttons: Contains username, password, and salt columns. - Transform using
sha256withSHA256+salt(prepend). - Output for storage or validation.
¶ Summary
The sha256 action is a flexible and secure hashing utility for ETL pipelines. It supports multiple hashing strategies based on your security needs—from plain hashing to secure keyed HMAC. Use it wherever you need to hash sensitive data such as passwords, tokens, or identifiers.
